Settings for Managing Multiple Projects
There are two approaches to connecting multiple Google Cloud projects:
- Inherit all permissions to Organization sub-projects: Manage all projects with a single service account.
- Delegate permissions to specific service accounts: Access multiple projects with one service account by establishing trust relationships between projects.
This document uses the following structure as an example to help understand the hierarchy:
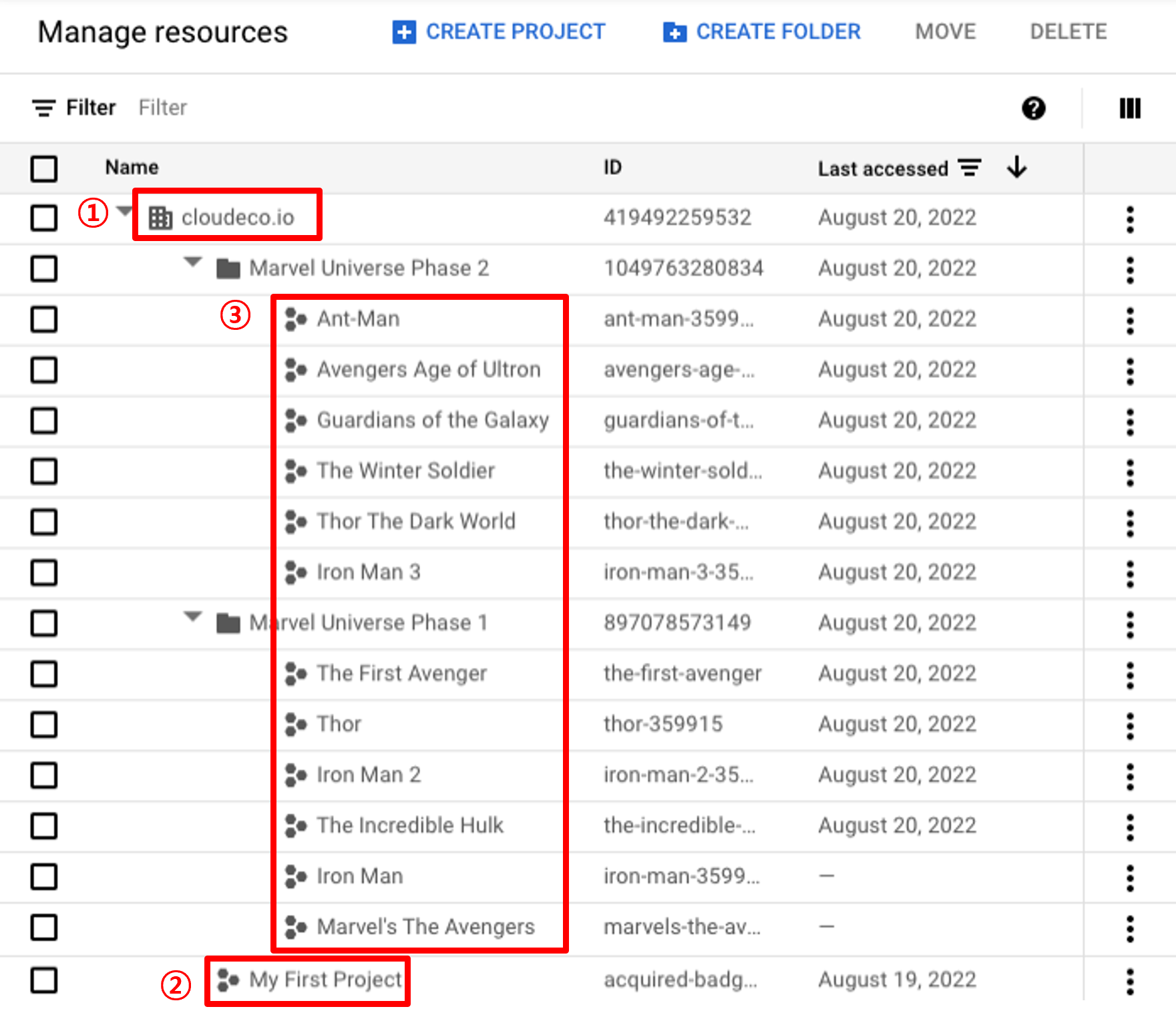
1️⃣ cloudeco.io: Top-level layer (Organization Level) for managing Google Cloud resources
2️⃣ Root Project: Project containing the service account for permission inheritance
3️⃣ Projects: Projects that inherit permissions from 2️⃣ Root Project
Inherit All Permissions to Organization Sub-projects
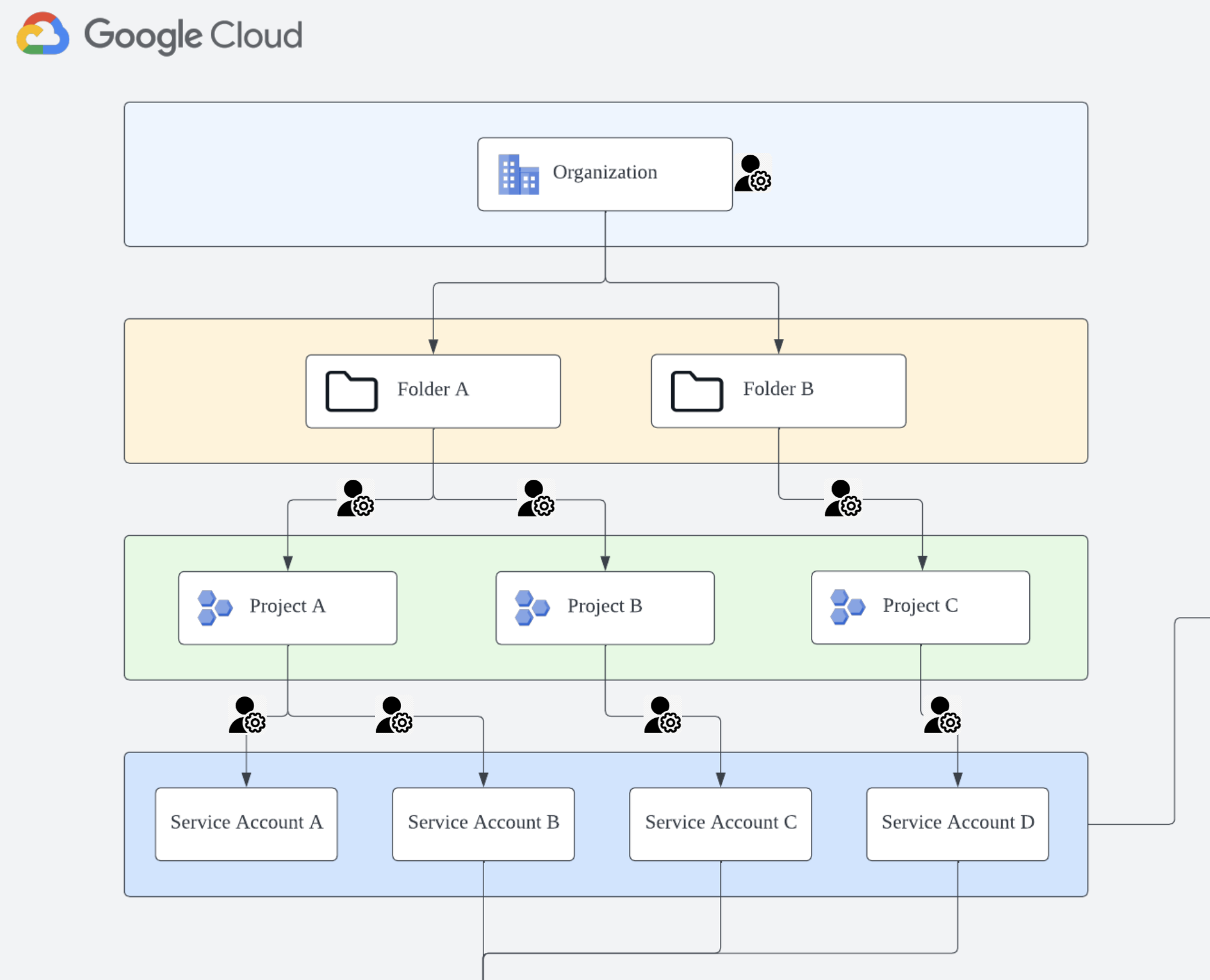 When you assign an IAM role at the Organization Level, all nodes (Folders and Projects) below inherit that role,
allowing you to manage all projects with a single service account (
When you assign an IAM role at the Organization Level, all nodes (Folders and Projects) below inherit that role,
allowing you to manage all projects with a single service account (2️⃣ Root Project).
Create Custom Role
Create a Custom Role in 1️⃣ cloudeco.io.
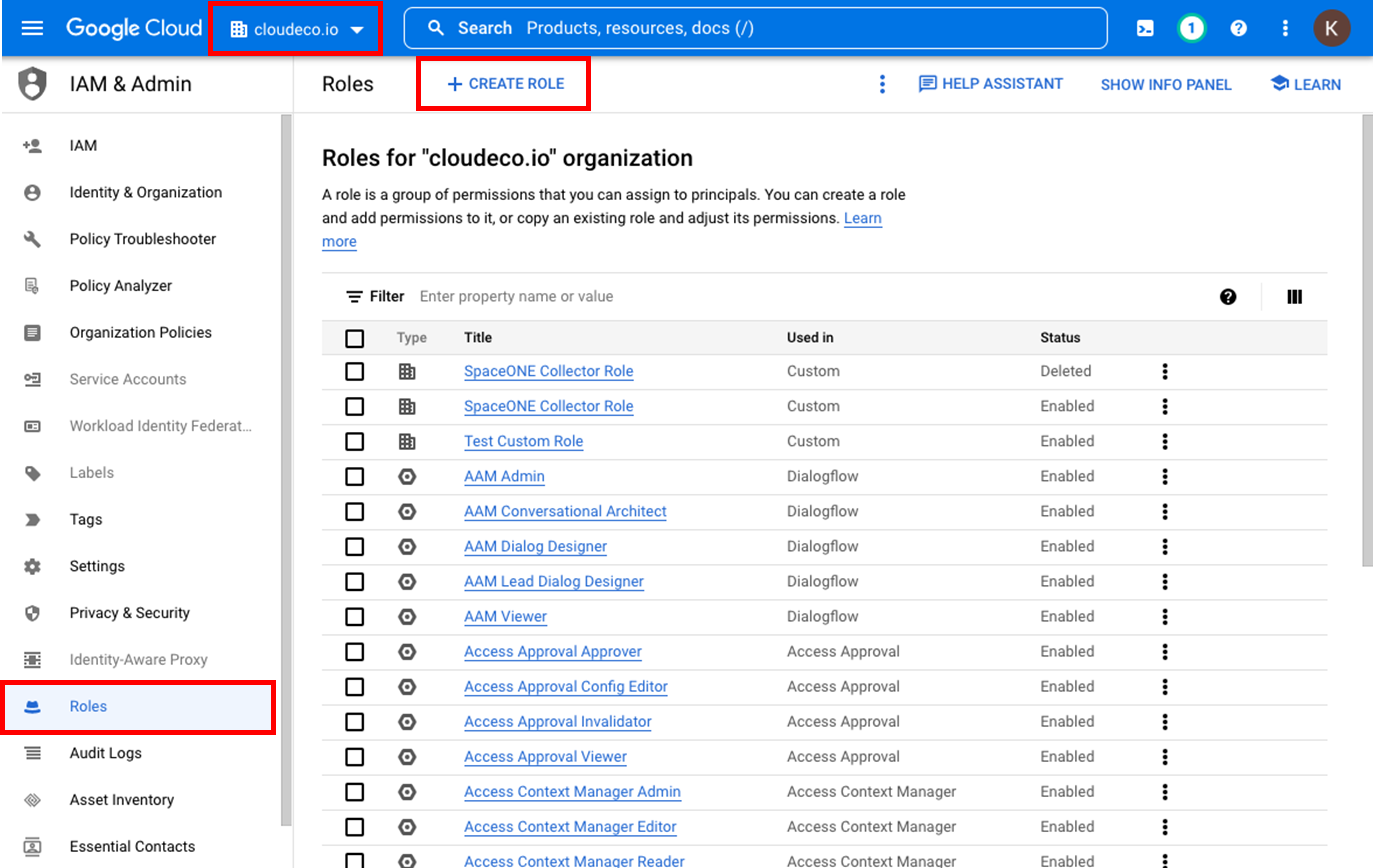
Search for the following [Name] values in the [Filter] search box to set up basic information and six permissions:
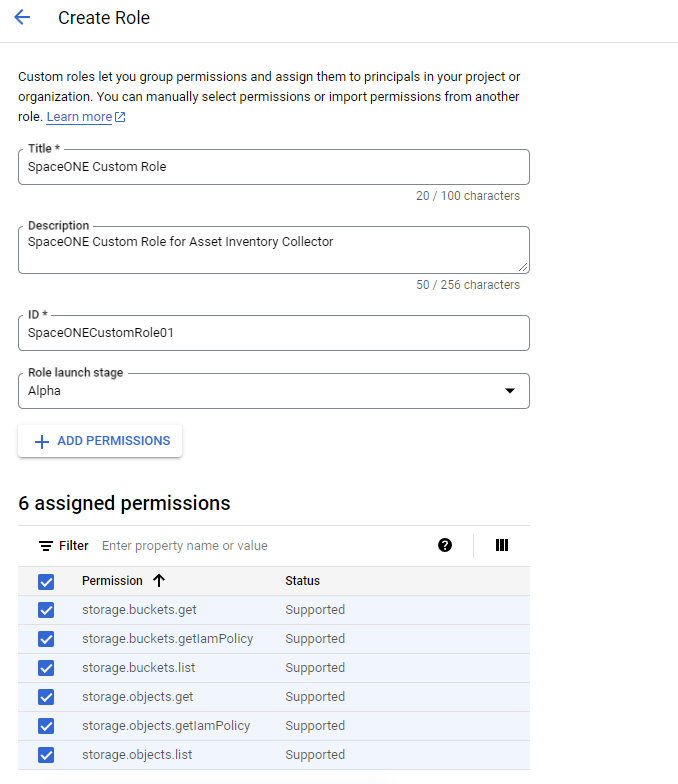
- storage.buckets.get
- storage.buckets.getIamPolicy
- storage.buckets.list
- storage.objects.get
- storage.objects.getIamPolicy
- storage.objects.listCreate Separate Project and Service Account for Permission Delegation
Create 2️⃣ Root Project and create a service account for permission inheritance in that project.
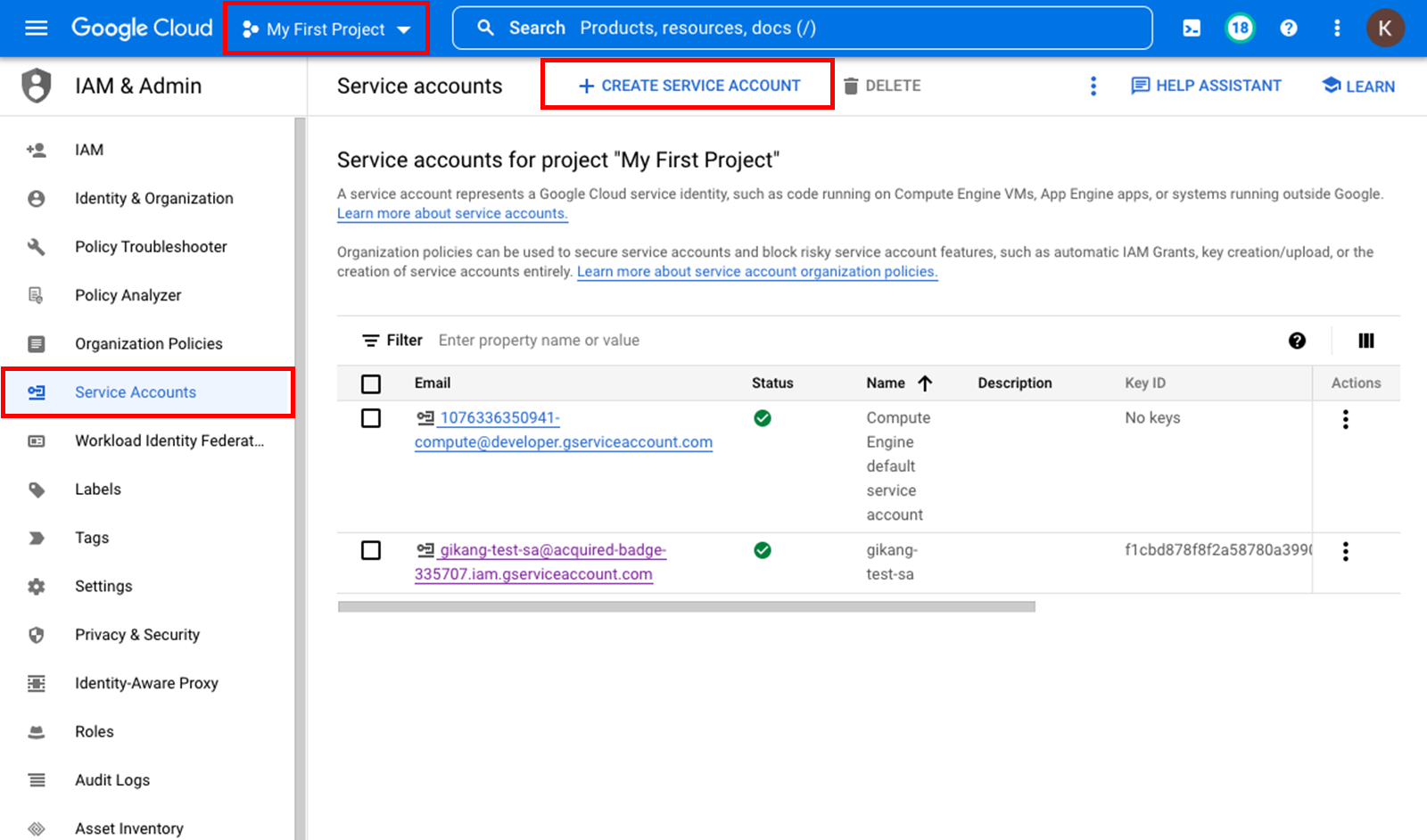
Enter basic information and set up the Custom Role created in Step 1 for SpaceONE integration.
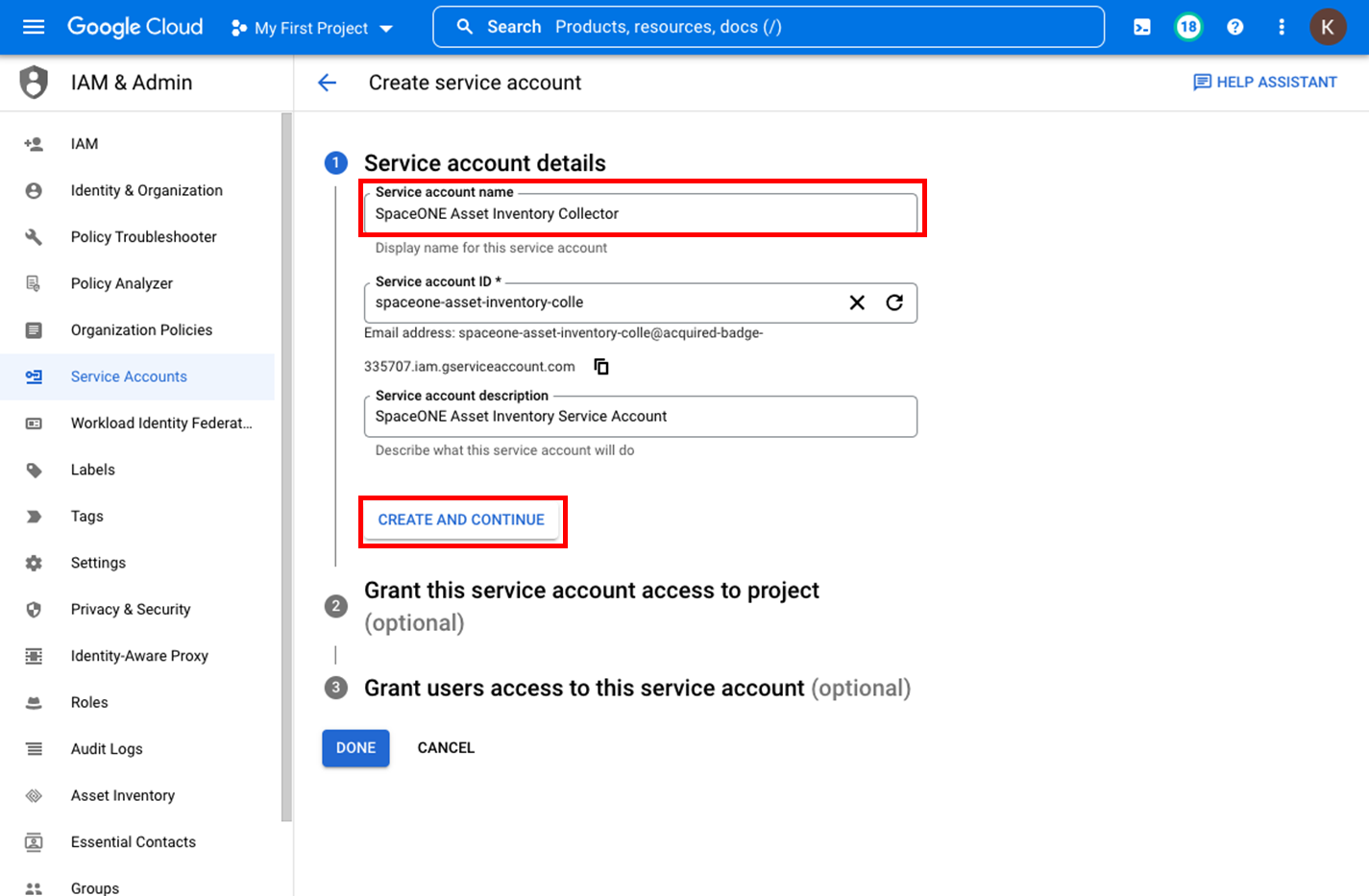
Search for the following [Name] values in the [Filter] search box to add permissions:
- SpaceONE Custom Role
- Compute Viewer
- Cloud SQL Viewer
- Environment and Storage Object Viewer
- Monitoring Viewer
- Pub/Sub Viewer
- Cloud Functions Viewer
- Cloud Asset Viewer
- Recommender ViewerEnable API Services
When registering a project directly to SpaceONE, the APIs for services in use are automatically enabled. However, for trust relationships, you must enable Google Cloud APIs for the delegated service account to properly collect resources.
Resources that require API enablement
Compute Engine | Networking | Cloud SQL | Storage | BigQuery | Cloud Pub/Sub | Cloud Functions | Recommender
- Go to Google Cloud Console API Library .
- Select the project you want to use from the project list.
- Select the API you want to use from the API Library.
- Click [Enable] on the API page.
Bind Delegated Service Account to 1️⃣ cloudeco.io
Add new Principal in [cloudeco.io > IAM > PERMISSIONS > ADD]
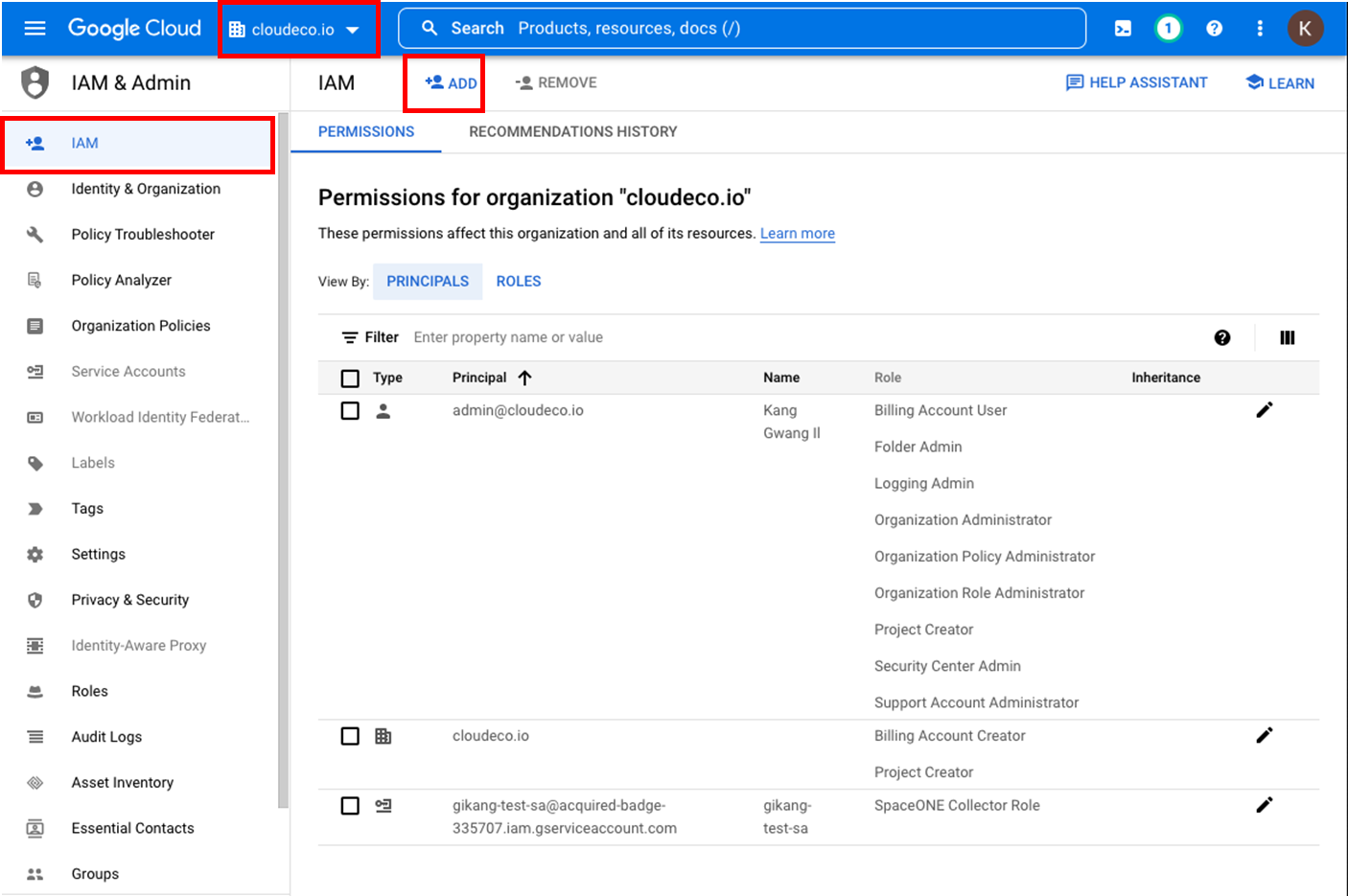
Enter the Service Account and role information created in Step 2
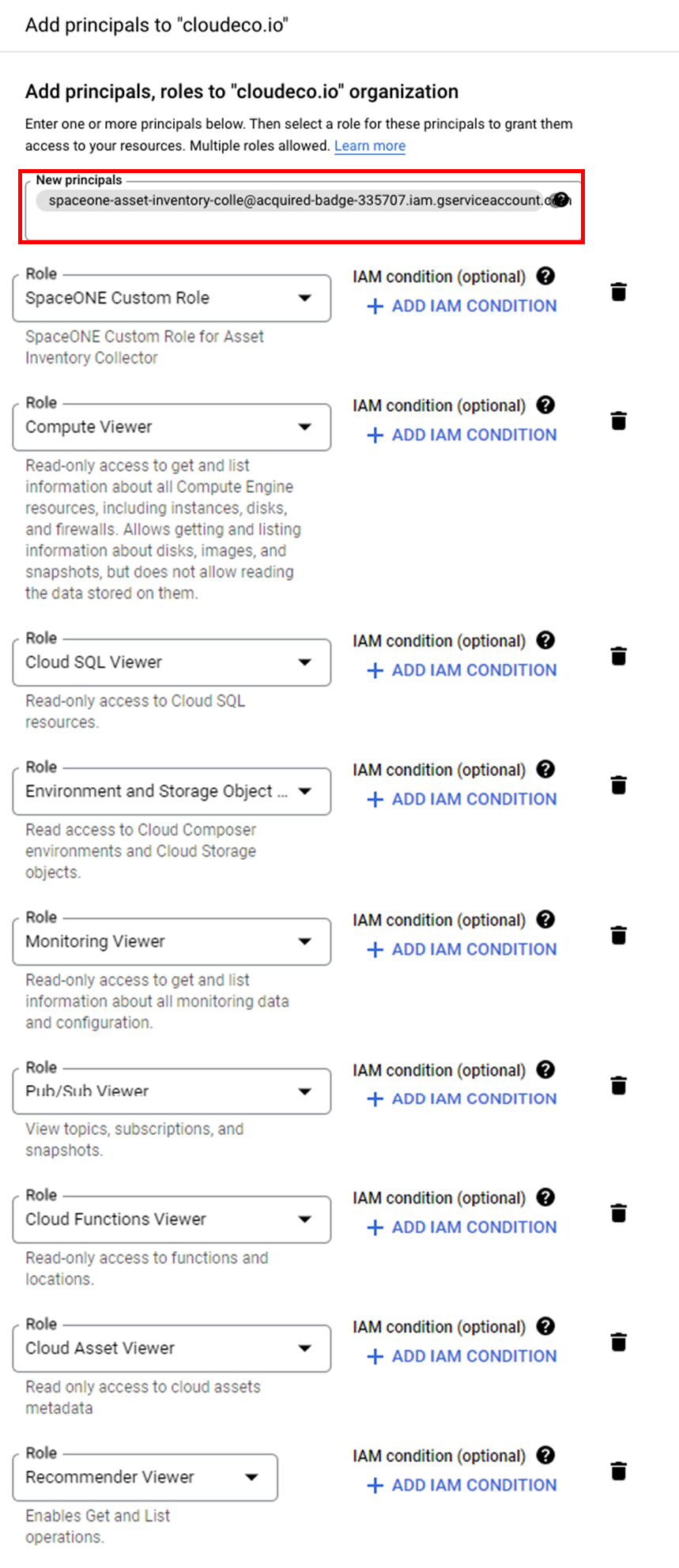
Once you’ve completed all these steps, the Google Cloud service account and roles will be inherited by all 3️⃣ Projects within 1️⃣ cloudeco.io.
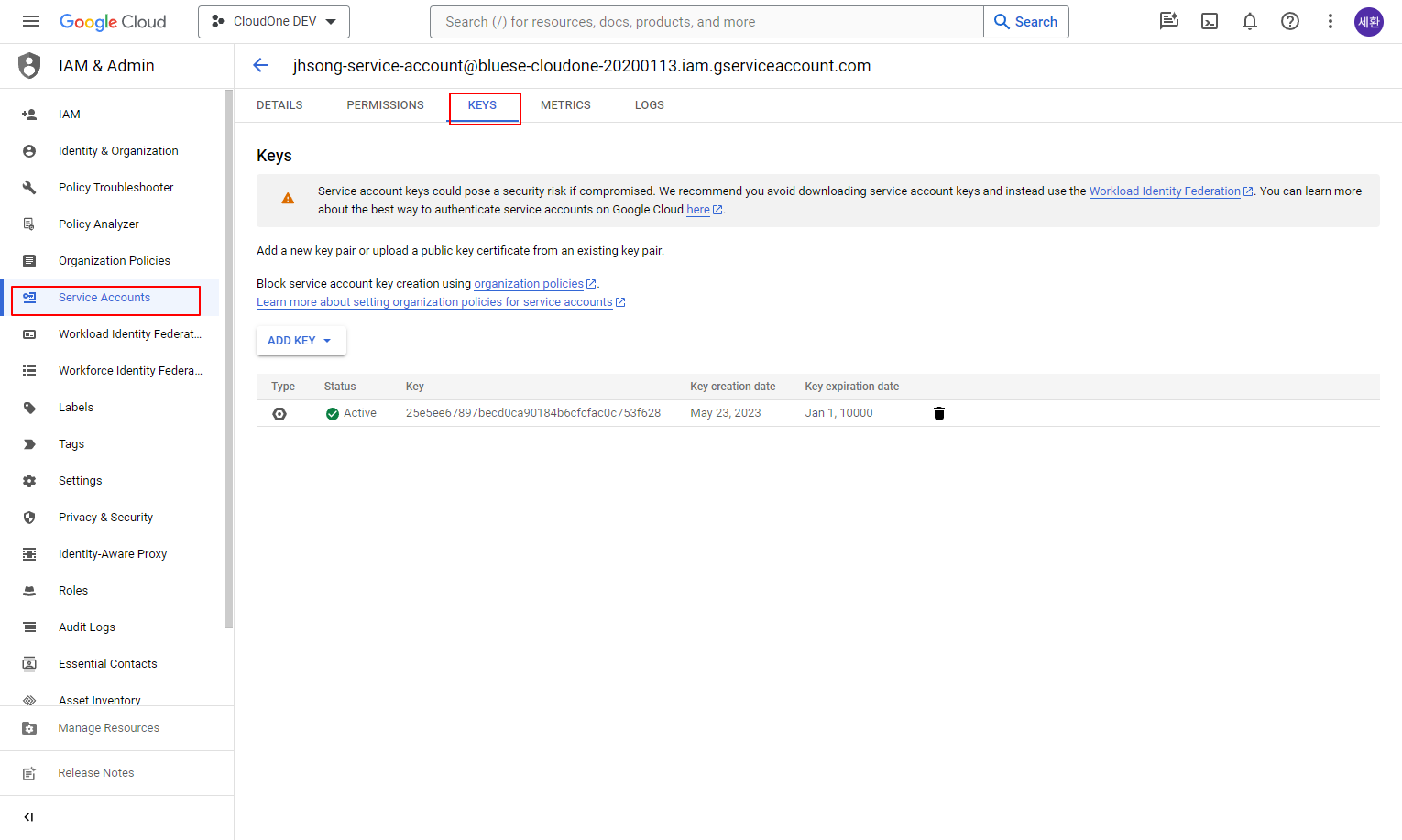
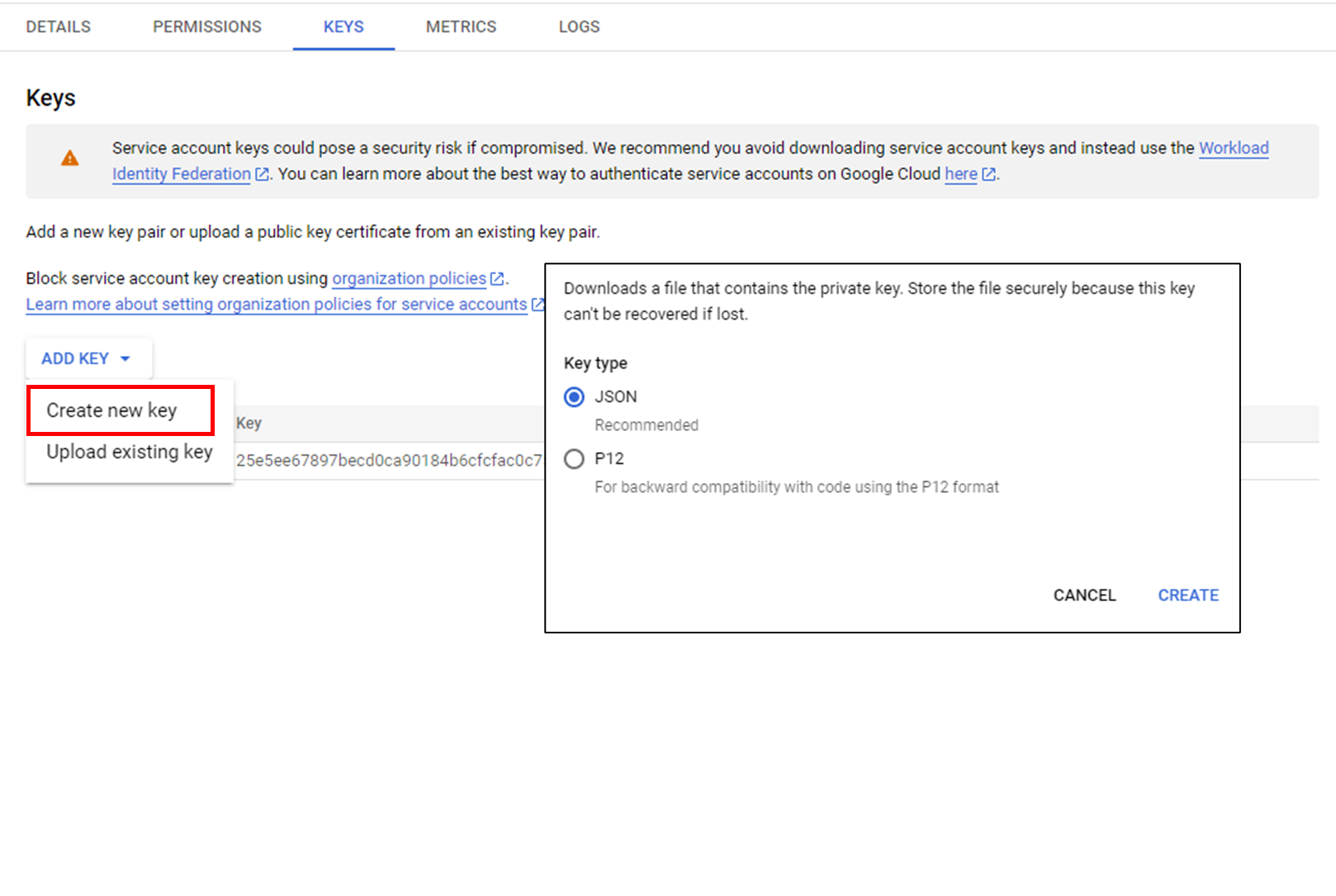
Download the service account’s authentication key in JSON format from [My First Project > Service Account > KEYS].
This will be used when registering a Trusted Account in SpaceONE.
Delegate Permissions to Specific Service Account
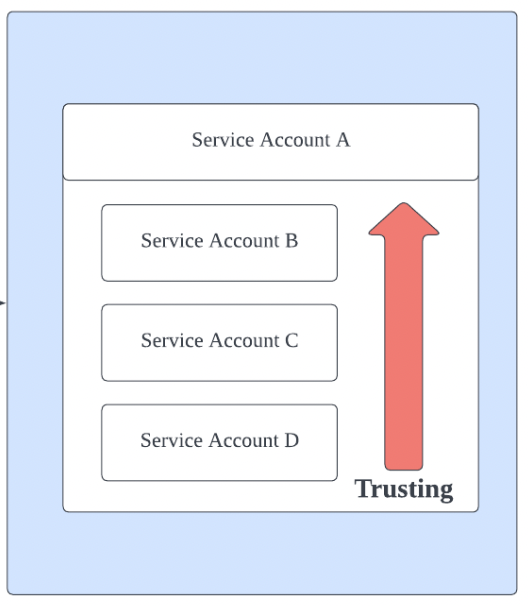
By setting up trust relationships between projects, you can connect Google Cloud service accounts in SpaceONE using only the Project ID without directly entering authentication key information.
When accessing General Accounts (3️⃣ Projects) that have a trust relationship with the Trusted Account (2️⃣ Root Project), SpaceONE references and utilizes the Trusted Account’s authentication key.
Navigate to Individual Projects
Move to the individual project that will establish a trust relationship with 2️⃣ Root Project.
Set Up Trust Relationship with 2️⃣ Root Project
In [IAM > GRANT ACCESS > Add Principals], add the 2️⃣ Root Project account as a member and grant Editor permissions.
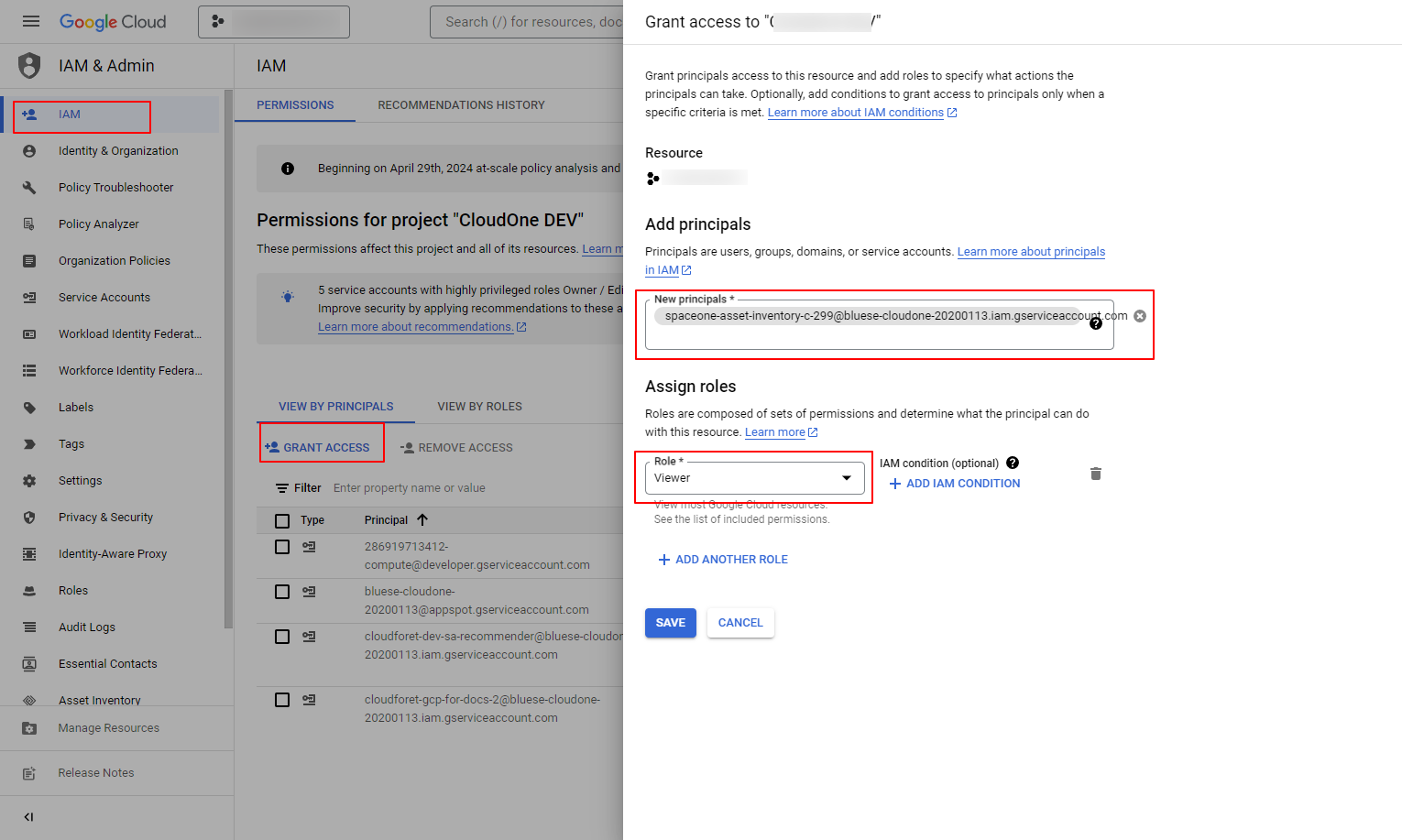
Repeat this process to establish trust relationships for all projects you want to connect to SpaceONE.