Access Key Method
Overview
The Access Key method requires the following configuration information:
Account ID
A unique 12-digit identifier that is automatically generated when creating an AWS account. For more details about Account ID, refer to AWS Documentation .
AWS Access Key & AWS Secret Key
Key values required to gain access to AWS API, CLI, SDK, and other development tools when creating an IAM account. For more details about AWS Access Key ID and AWS Secret Key, refer to AWS Documentation .
The complete setup process follows this order:
- Create IAM Policy
- Create IAM User
- Create IAM Group
The collector plugin requires only read permissions and no other permissions. Information about the permissions required by each plugin is as follows:
| Plugin | URL |
|---|---|
| AWS Cloud Services collector | https://github.com/cloudforet-io/plugin-aws-cloud-service-inven-collector#authentication-overview |
| AWS EC2 Compute collector | https://github.com/cloudforet-io/plugin-aws-ec2-inven-collector#authentication-overview |
| AWS Personal Health Dashboard collector | https://github.com/cloudforet-io/plugin-aws-phd-inven-collector#authen |
| AWS Trusted Advisor collector | https://github.com/cloudforet-io/plugin-aws-trusted-advisor-inven-collector |
1. Create IAM Policy
Access AWS Console
Access the AWS Console .
Create IAM Policy
You can create policies in the [Access Management > Policies] menu of the dashboard.
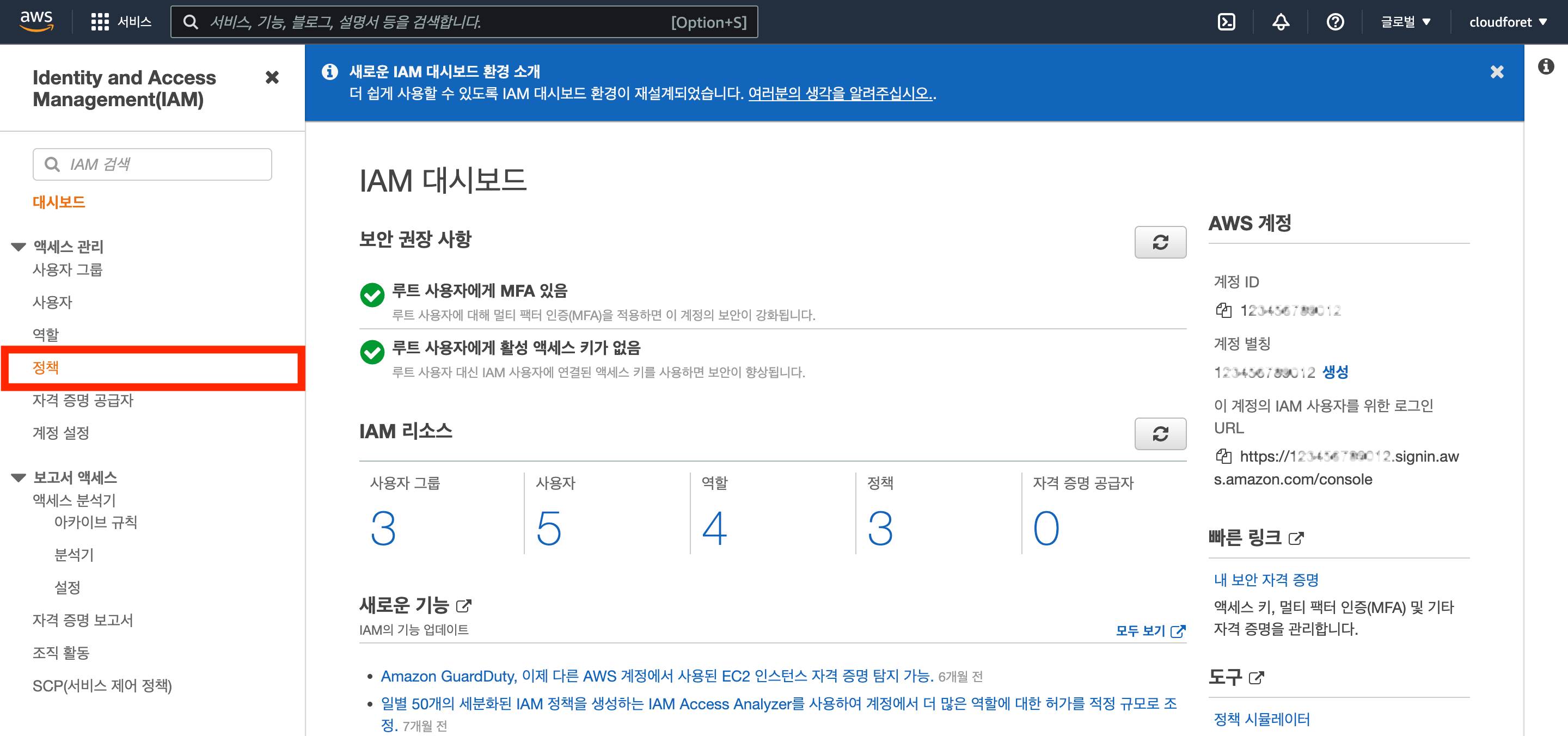
Set Policy Permissions
Click the [Create Policy] button to create a policy.
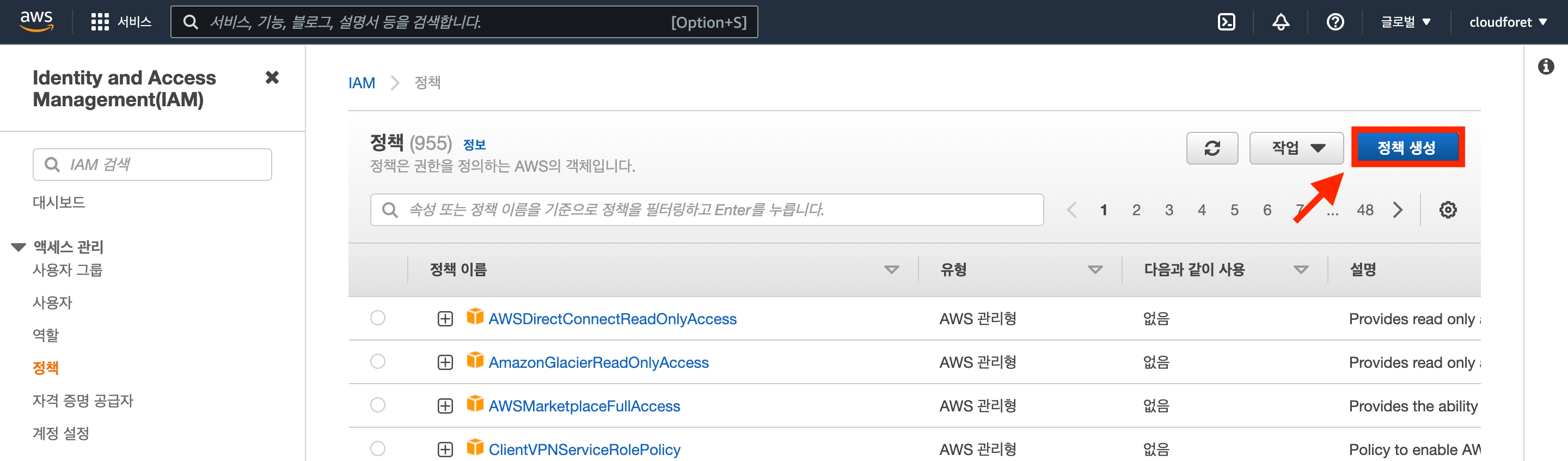
(1) Click the [JSON] tab to grant permissions for this policy.
(2) Copy the permission list for the specific plugin from the table above and click [Next: Tags].
- You can create permissions for all four plugins or select specific plugins.
- For basic AWS service collection, it is recommended to set up
AWS Cloud Services collectorandAWS EC2 Compute collector.
When Permission Definition Error Occurs
This policy contains the following error: JSON strings must not have leading spaces. For more information about the IAM policy grammar, see AWS IAM Policies
If you encounter this error, delete the leading space in the first line of the code block.
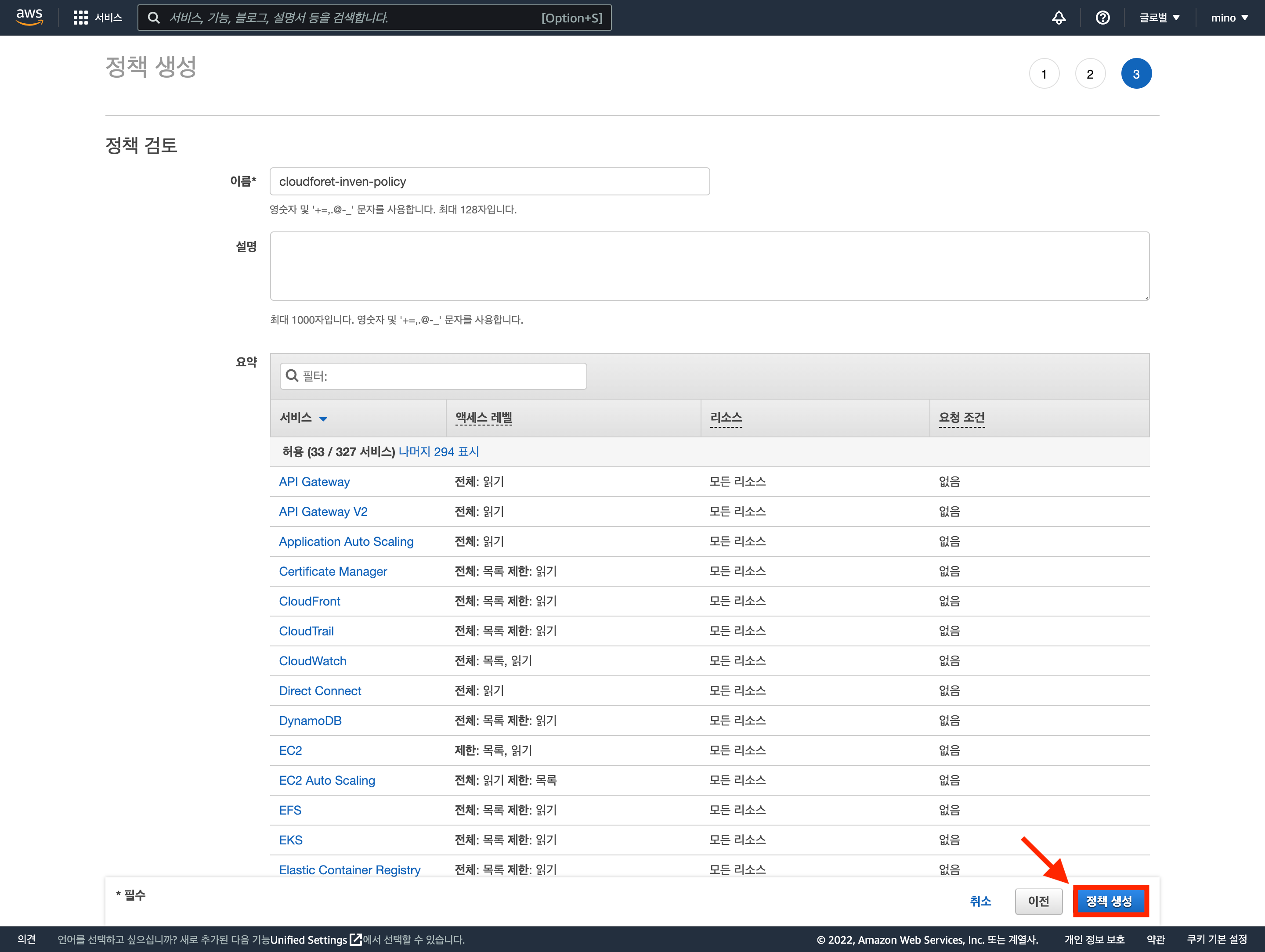
Review and Create Policy
(1) If there is no separate tag-based management policy, click [Next: Review].
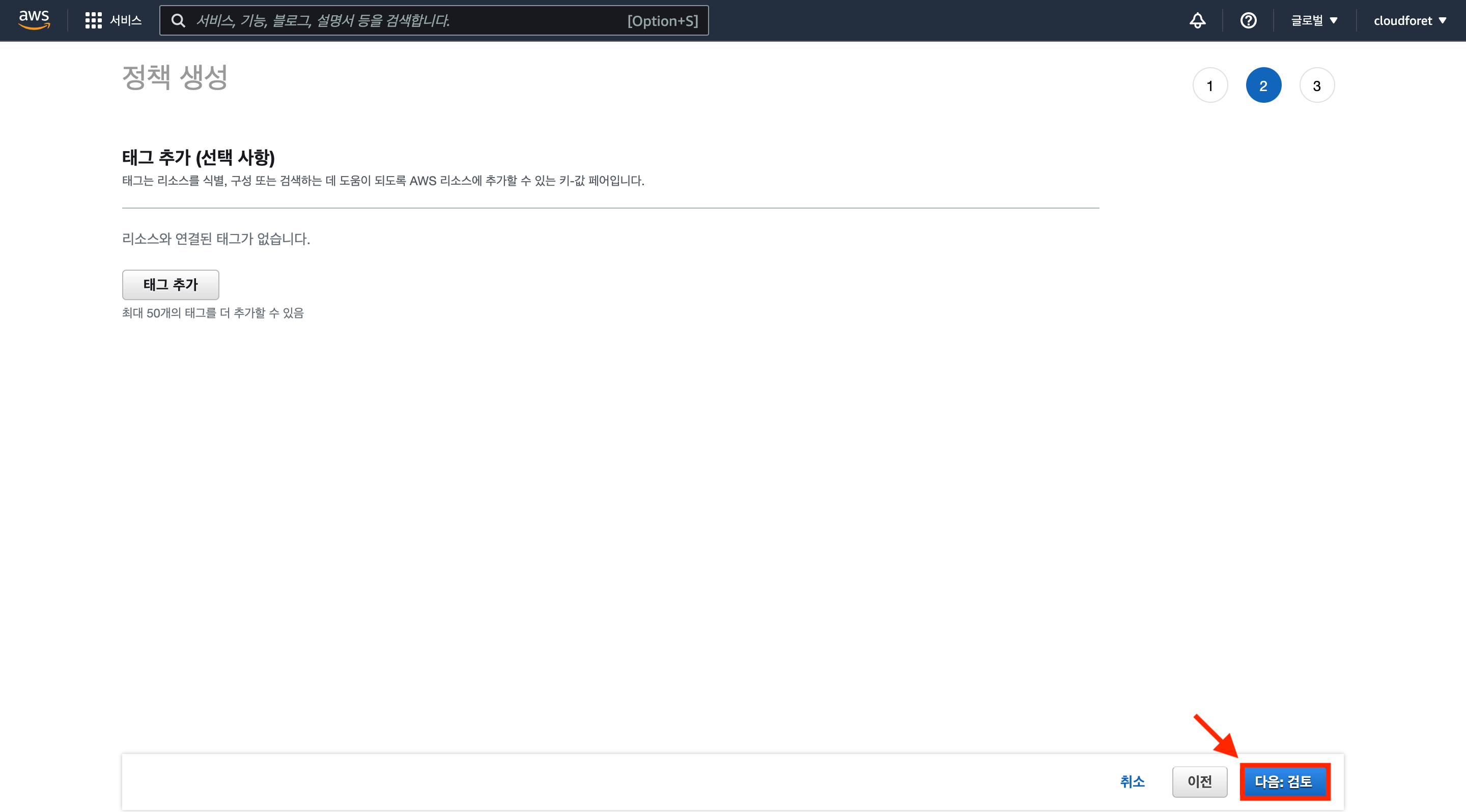
(2) Enter the policy name and click [Create Policy] to complete policy creation.
2. Create IAM User
AWS Access Key ID and AWS Secret Key which are required when registering a service account.IAM users are created to securely control access to AWS resources. The created IAM user will be added to a group in the next step.
Access AWS Console
Access the AWS Console.
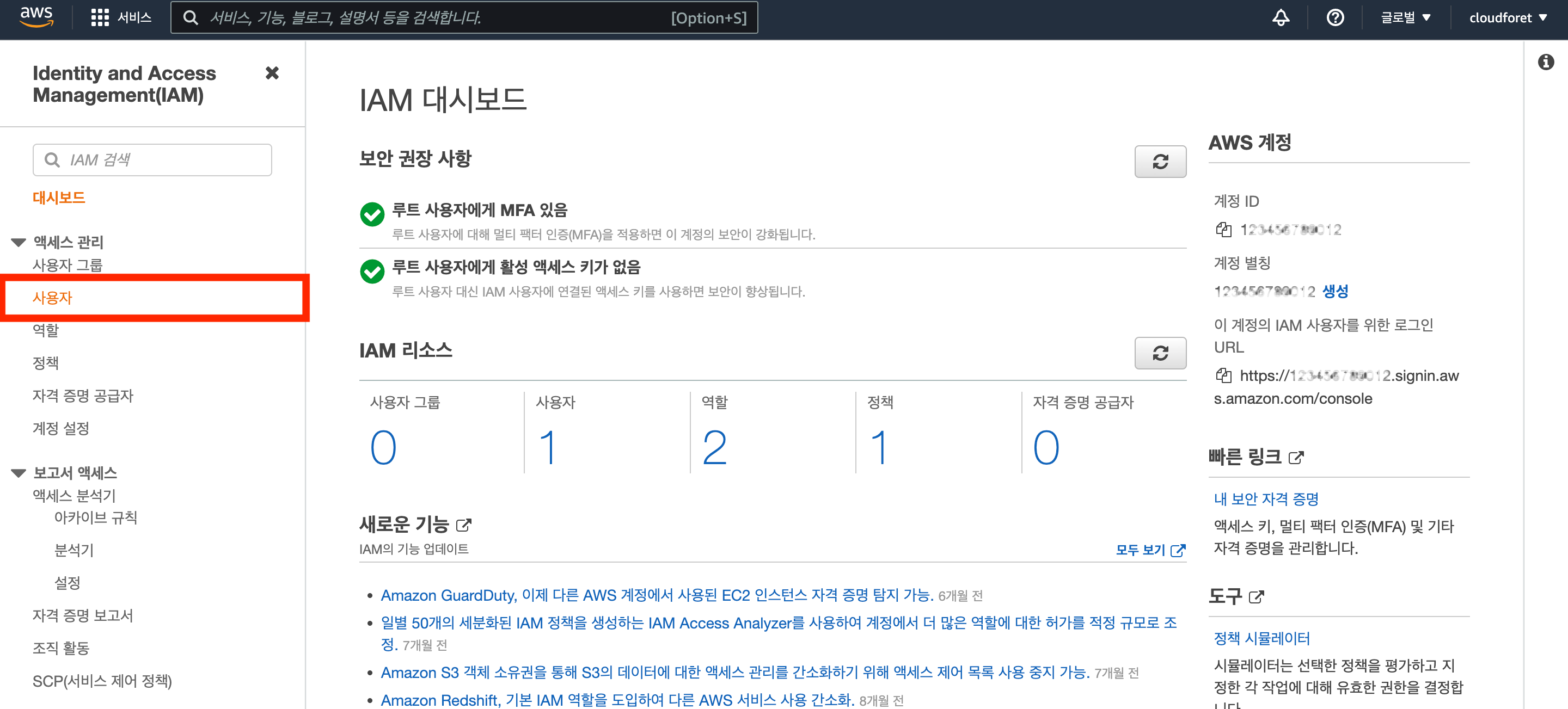
Create IAM User
Click the [Add User] button in the [Access Management > Users] menu of the dashboard.
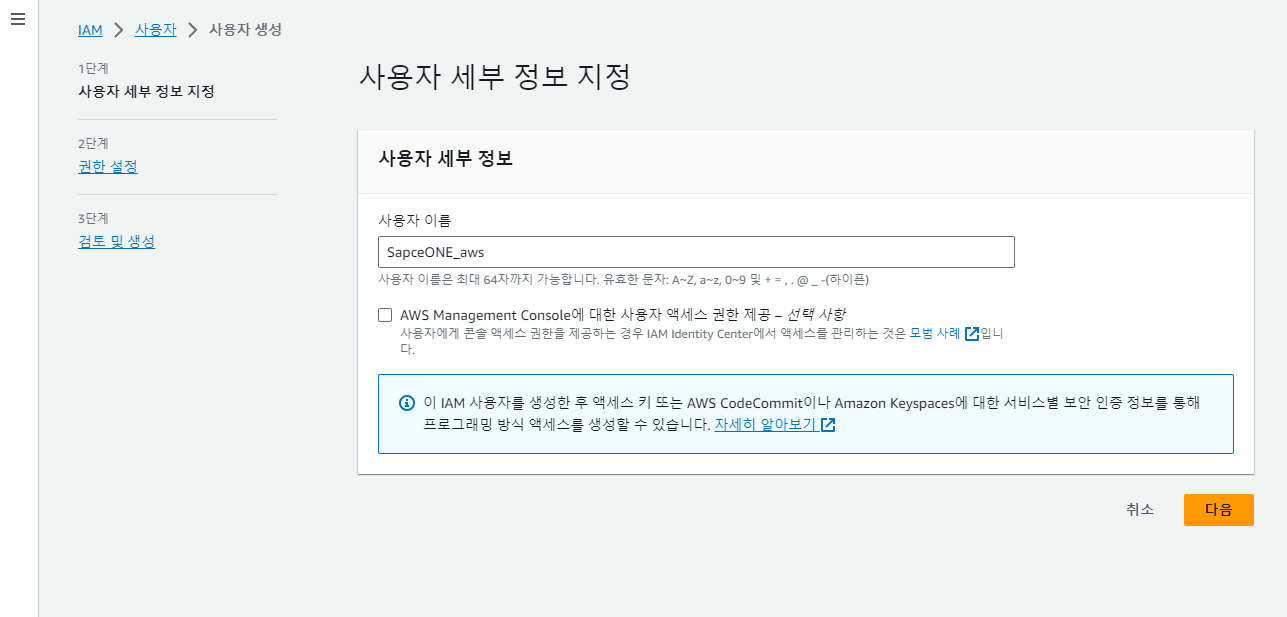
Configure User Details
(1) Enter the username and click [Next].
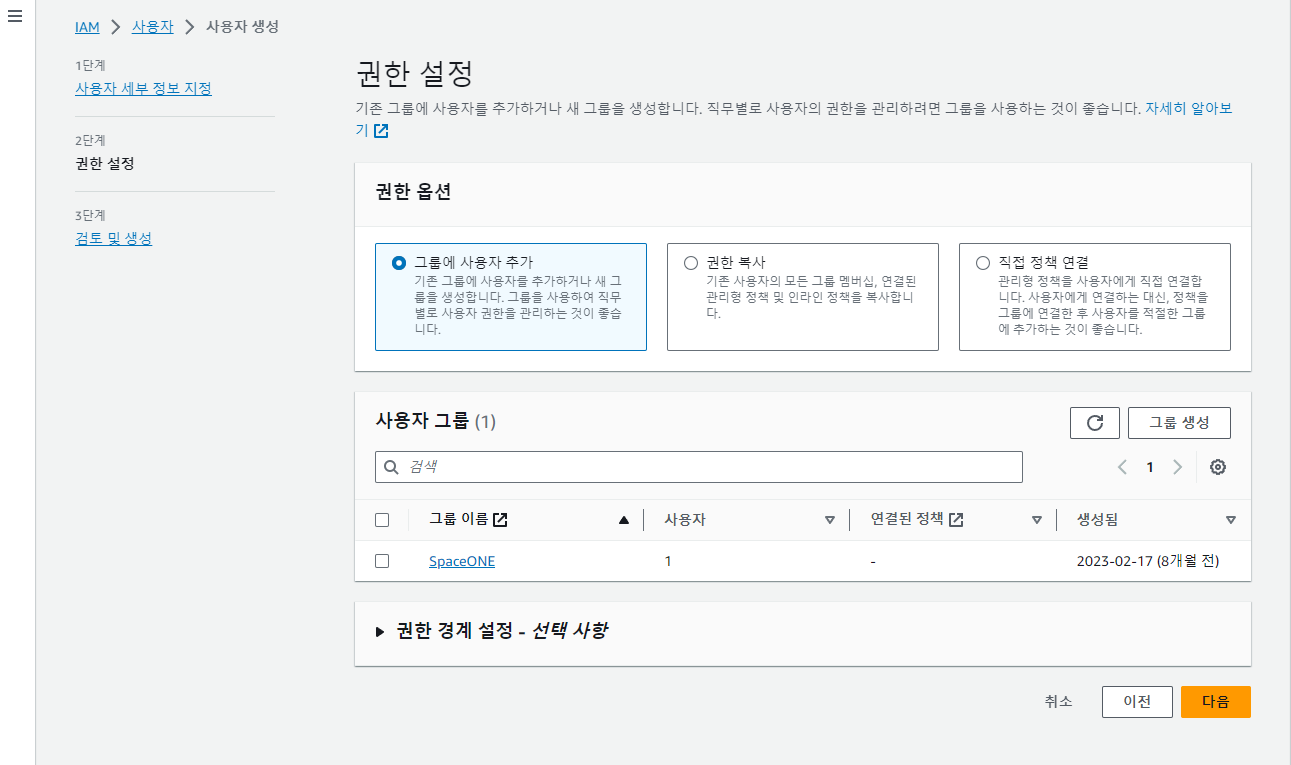
(2) Do not add the user to a group at this stage. Click [Next].
(3) If there is no separate tag-based management policy, skip and click [Create User].
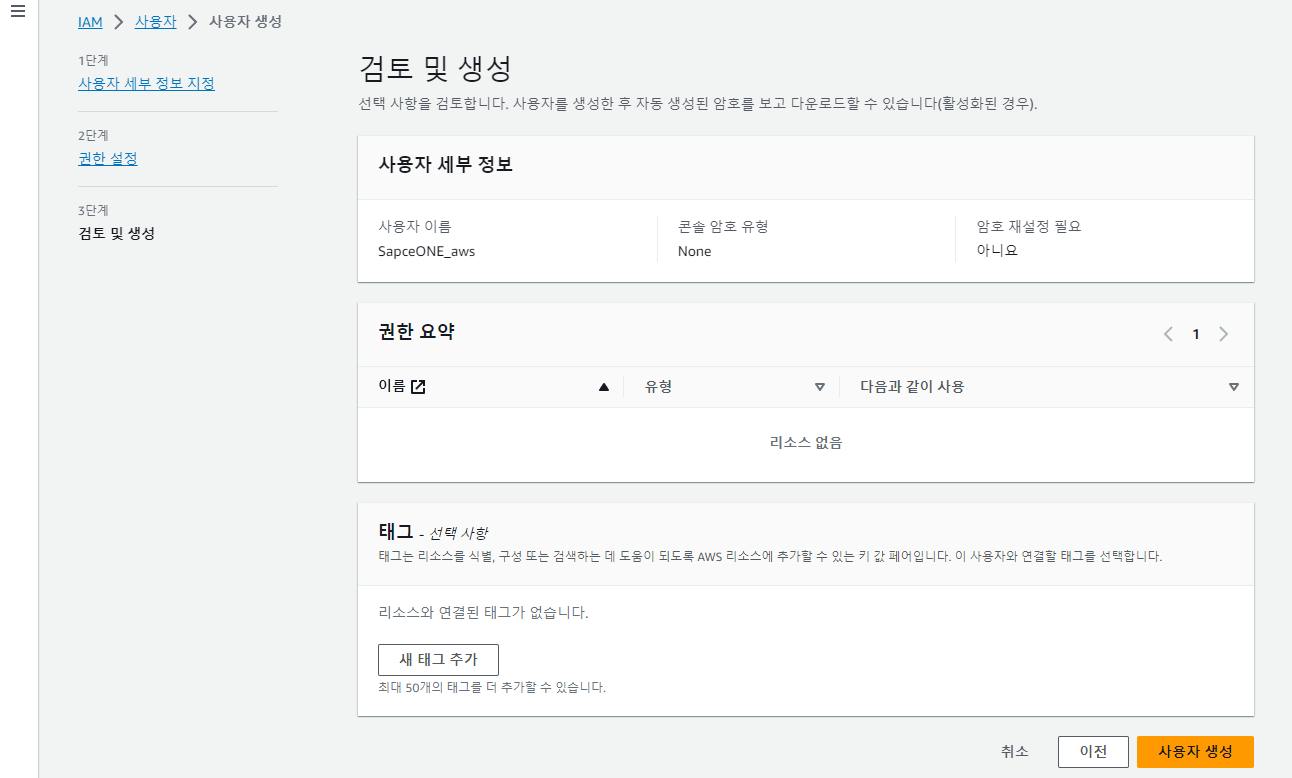
- Do not set permissions for the IAM user at this stage.
- In the 3. Create IAM Group step, you will grant permissions to users by adding policies to the group.
Verify Access Keys
The [Access Key ID] and [Secret Access Key], which are the configuration information corresponding to [AWS Access Key ID] and [AWS Secret Key] required for service account registration, will be created.
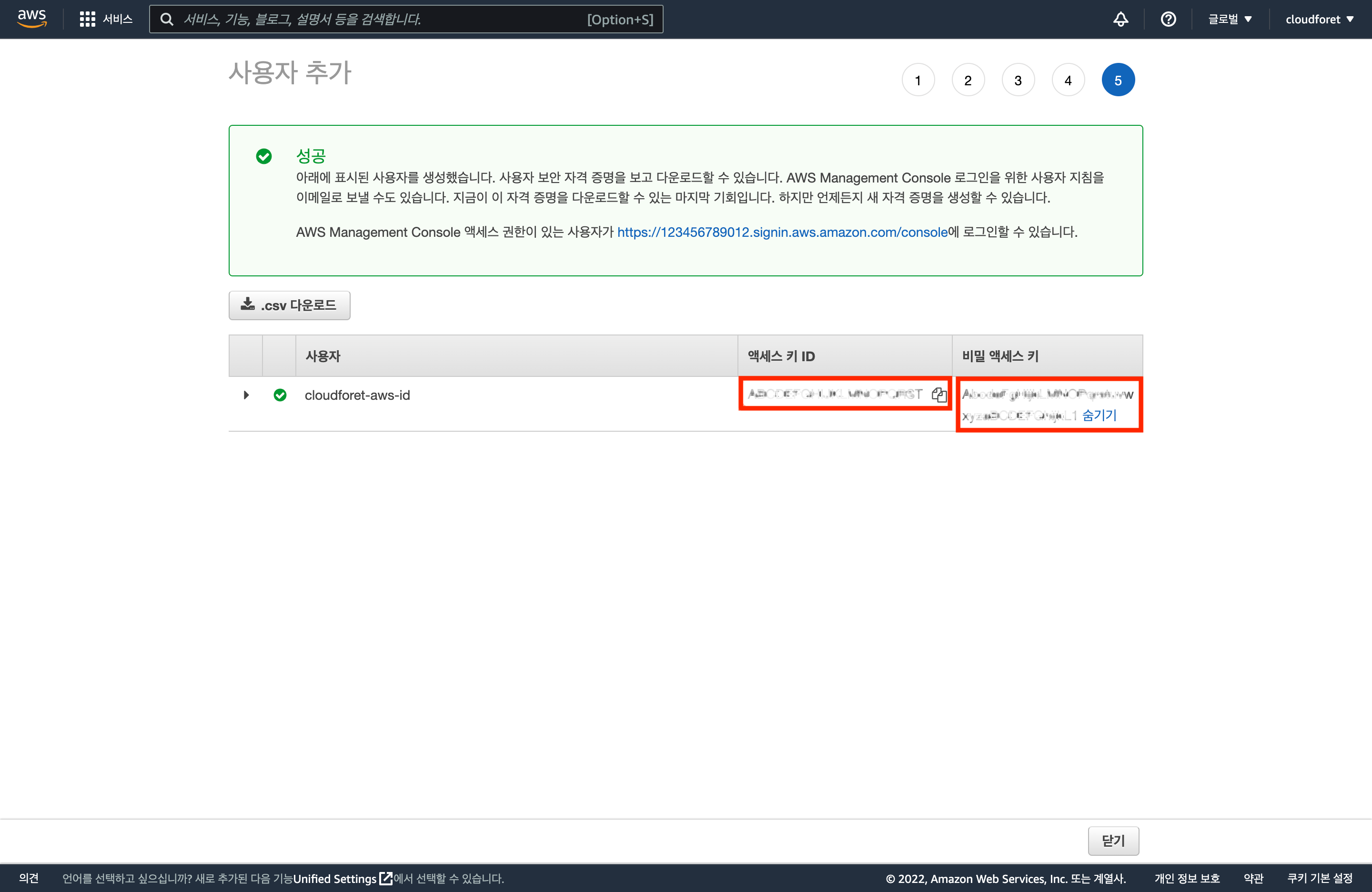
- Please make sure to note these values as you won’t be able to see them again after leaving this page.
- These Key values are essential for the SpaceONE Service Account Registration step.
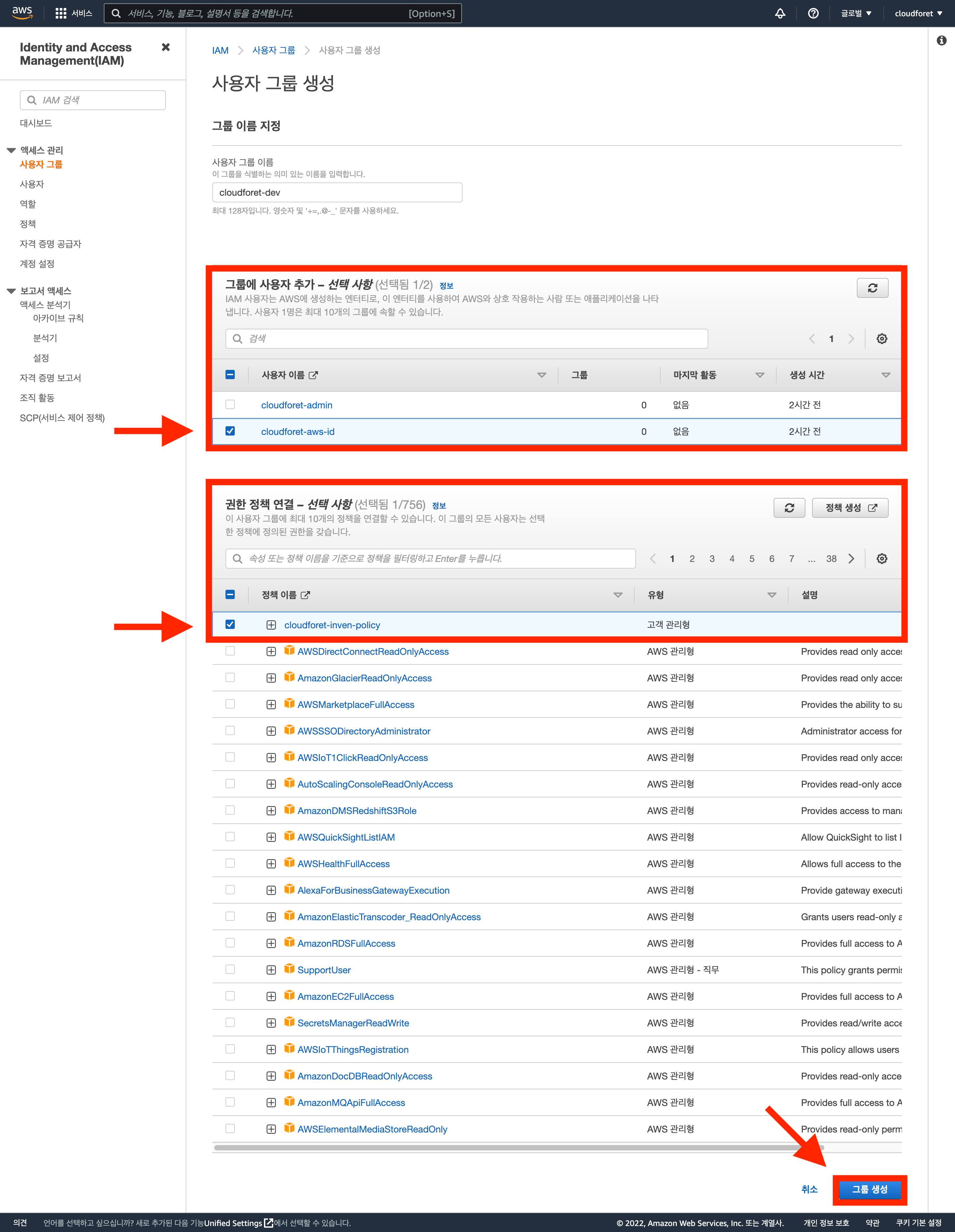
3. Create IAM Group
A Group is a collection of IAM users. Through groups, you can specify permissions for users and more easily manage permissions for those users.
Access AWS Console
Access the AWS Console .
Create IAM Group
Click the [Create Group] button in the [Access Management > User Groups] menu of the dashboard.
Configure Group Details
Select the user created in 2. Create IAM User and the policy created in 1. Create IAM Policy, then click [Create Group].
For future users, you can apply the policy-configured group at this stage.